- Scattered Spider is targeting insurance firms through malicious OAuth apps that bypass MFA and appear legitimate.
- Their tactics exploit open SaaS marketplaces—already causing $100M+ losses per org.
- EU insurers are likely next. Attack surface is expanding fast.
- DeepOpinion’s governed integration model and agentic architecture provide built-in defense.
Disclaimer: The following demonstration is intended solely for educational and authorized security research in controlled environments. It should not be replicated in production systems or used without proper authorization.
A Growing Alarm in the Threat Landscape
At DeepOpinion, our security, compliance and engineering teams maintain constant vigilance over the evolving threat landscape, monitoring emerging attack patterns that could impact both our organization and our customers. Recently, we’ve observed a concerning trend that has escalated our threat assessment: the cybercriminal collective known as Scattered Spider has begun systematically targeting insurance companies across the United States.
This shift represents more than just another sector being attacked—it signals a strategic evolution in one of the most sophisticated and successful threat actors of the modern era. Based on historical patterns, we anticipate this campaign will likely expand to insurance and broader Banking, Financial Services, and Insurance (BFSI) sectors across the European Union in the coming months.
What makes this particularly alarming is not just who Scattered Spider targets, but how they operate. This isn’t a traditional cybercriminal organization with hierarchical command structures. Instead, Scattered Spider represents something more dangerous: a distributed methodology that combines masterful social engineering with an intimate understanding of the modern SaaS ecosystem that unlike DeepOpinion often offers unsolicited apps to be added to it’s market place and integrations and increasingly forms the backbone of enterprise operations.

Understanding Scattered Spider: A Methodology, Not Just a Group
To understand the threat Scattered Spider poses, we must first recognize what they truly are. Despite the singular name, Scattered Spider is better understood as a loose collective of individuals—primarily young, English-speaking attackers from the US, UK, Canada, and Australia, many in their teens to early twenties. They operate more like a shared playbook than a traditional criminal organization.
This distributed nature is precisely what makes them so resilient. When law enforcement arrested several key members in 2024, including alleged leader Tyler Buchanan in Spain and others across multiple jurisdictions, the attacks didn’t stop. New individuals simply adopted the proven methodologies, continuing operations with barely a pause. The group’s techniques have become so effective that they’ve essentially created a replicable attack framework that others can implement.
Their track record speaks to this effectiveness:
- MGM Resorts (September 2023): A 36-hour system outage resulting in over $100M in losses and 6TB of stolen data
- Caesars Entertainment (August 2023): $15M ransom payment after customer database compromise
- Transport for London (September 2024): 5,000 users’ bank details exposed, 30,000 staff requiring password resets
- UK Retail Campaign (2025): Marks & Spencer alone suffered £300M in lost profits and £1B in share value impact
The Perfect Storm: Modern SaaS Ecosystems as Attack Vectors
What makes Scattered Spider particularly dangerous in today's enterprise environment is their deep understanding of how modern businesses operate. Organizations increasingly rely on complex webs of Software-as-a-Service (SaaS) applications, many of which—unlike DeepOpinion—have internal marketplaces and integrations that allow for unsolicited additions, each connected through identity and access federation systems that provide seamless access to vast amounts of data.
This interconnected ecosystem, while enabling unprecedented productivity and collaboration, has created new attack surfaces that traditional security measures struggle to address. OAuth integrations, API access tokens, and third-party application marketplaces have become the new frontier for sophisticated attackers.
To demonstrate just how realistic and widespread this threat is, our security team developed a proof-of-concept that simulates a Scattered Spider-style attack targeting SaaS integrations. While our demo uses Notion as an example, the attack methodology applies to virtually any SaaS platform with an integration marketplace—Slack, Microsoft 365, Google Workspace, Salesforce, and countless others.
Anatomy of a Modern SaaS Attack: A Realistic Demonstration
To illustrate the severity and accessibility of this threat, our security team developed a fully functional proof-of-concept that demonstrates how easily these attacks can be executed. The complete source code for our demonstration is available on GitHub, with strict disclaimers that it should only be used for educational purposes in controlled environments with explicit authorization.
What makes this attack particularly concerning is how simple it is to set up. The screenshot below shows Notion's integration creation interface, where anyone can register a new application with extensive permissions. This process takes mere minutes and requires no verification of the developer's identity or intentions:
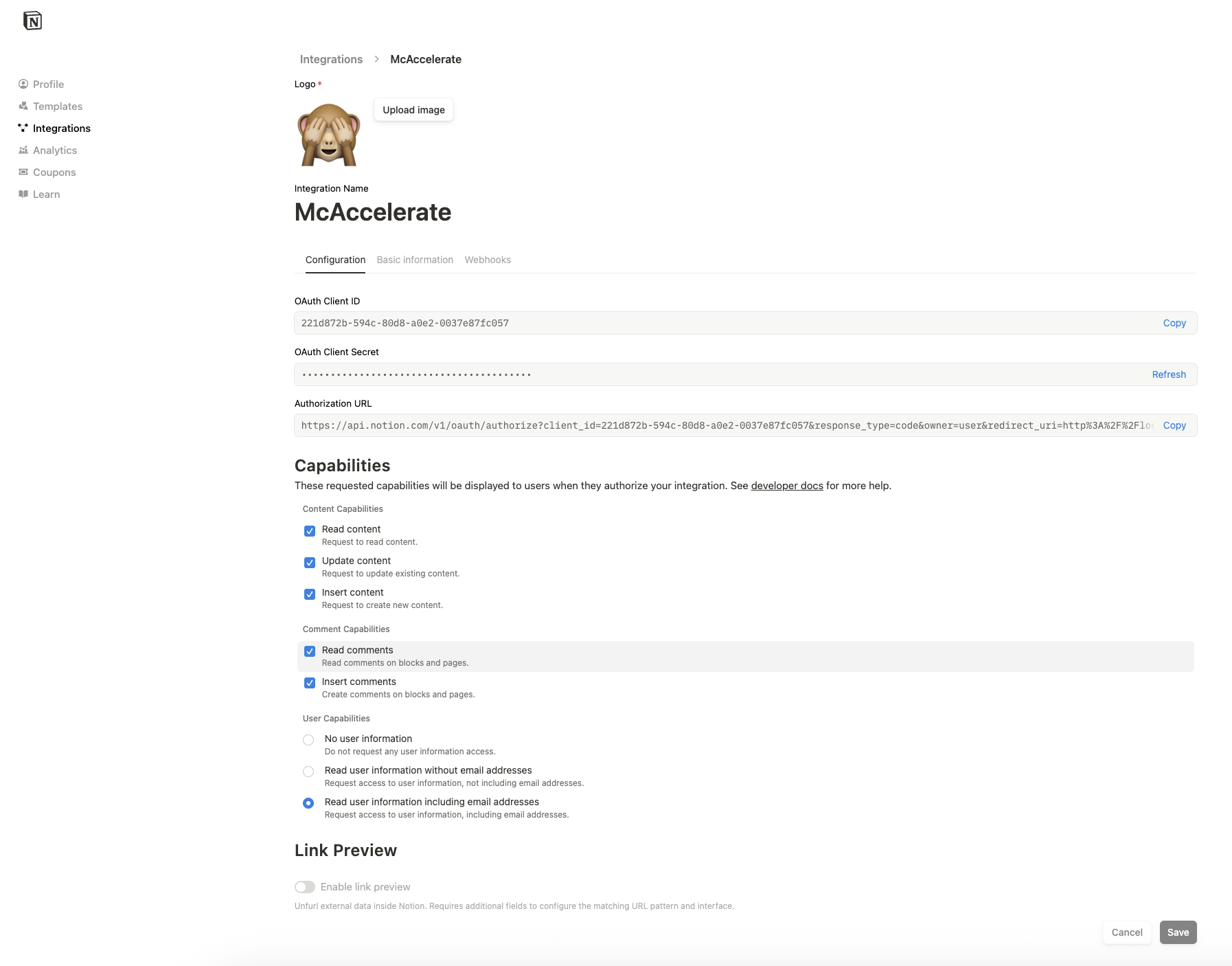
The ease of creating legitimate OAuth applications with extensive permissions demonstrates a fundamental vulnerability in the SaaS ecosystem. Once an application is registered, it can be used globally to target any Notion workspace, making the attack scalable across thousands of potential victims.
Our proof-of-concept demonstrates a four-stage attack that mirrors real-world Scattered Spider tactics:
Stage 1: The Phishing Hook
The attack begins with a carefully crafted email that exploits common business pain points. In our demo, the attacker poses as “McAccelerate,” offering enterprise Notion features at startup prices—a compelling proposition for cost-conscious organizations.
The email demonstrates sophisticated social engineering:
- Personalization: References the target company’s industry and growth
- Pain Point Exploitation: Addresses real concerns about enterprise software costs
- Urgency Creation: Limited-time offers and scarcity tactics
- Professional Presentation: Legitimate-looking branding and messaging
Stage 2: The Convincing Landing Page
Victims are directed to a professional-looking application page that appears to be a legitimate SaaS tool. The page includes:
- Trust indicators (customer counts, compliance badges)
- Feature lists that address real business needs
- Professional design that mirrors legitimate SaaS applications
- A prominent “Connect with Notion” OAuth button
Stage 3: Legitimate OAuth Authorization
Here’s where the attack becomes particularly insidious. When users click the connection button, they’re redirected to Notion’s actual OAuth consent screen—not a fake page, but the real authorization flow. The malicious application requests seemingly reasonable permissions to deliver on it’s promises:
- Read all pages and databases
- Create and edit pages
- Access shared workspaces
- Read user information
To most users, these permissions appear necessary for the promised functionality. The OAuth flow is legitimate, the permissions seem reasonable, and the consent screen is from the trusted SaaS provider.
Stage 4: Data Exfiltration Through Legitimate APIs
Once authorized, the malicious application gains full API access to the organization’s Notion workspace with the user’s exact scope. Our demonstration shows the extraction of:
- User Data: Complete employee directory with names, roles, and contact information
- Workspace Content: All pages, documents, and collaborative content
- Database Information: Structured data including customer information, project details, and business intelligence
- Comments and Discussions: Private conversations and internal communications
The critical point is that all of this data access occurs through legitimate API calls. From a security monitoring perspective, these requests appear completely normal—because they are normal API usage, just by an unauthorized party.
Why This Attack Circumvents Traditional Security Measures
This attack methodology is particularly effective because it bypasses multiple layers of traditional security controls:
Multi-Factor Authentication (MFA) Bypass
OAuth flows often bypass MFA requirements because the user has already authenticated with the SaaS provider. Once the application is authorized, it can access data using API tokens without requiring additional authentication.
Detection Evasion
Security teams monitoring for suspicious activity will see legitimate API calls from an authorized application. There are no failed login attempts, no unusual access patterns, and no technical indicators of compromise—just normal API usage.
User Trust Exploitation
Users are conditioned to trust OAuth flows from legitimate SaaS providers. When they see Notion’s actual consent screen, they assume the application must be legitimate because it’s using official authorization mechanisms.
The Integration Marketplace Problem
A critical vulnerability in the modern SaaS ecosystem is the open nature of integration marketplaces. Most major SaaS platforms allow anyone to create and publish integrations, creating numerous opportunities for malicious actors:
Typosquatting and Name Collision
Attackers can create applications with names similar to legitimate tools:
- “NotionBoost” instead of “Notion Boost”
- “SlackEnhancer” instead of “Slack Enhancer”
- “TeamsOptimizer” instead of “Teams Optimizer”
Fake Sales and Marketing Campaigns
Sophisticated attackers create entire marketing campaigns around their malicious applications, including:
- Professional websites and documentation
- Social media presence and testimonials
- Email marketing campaigns targeting specific industries
- Conference presentations and thought leadership content
IT Impersonation
Attackers may impersonate internal IT teams, requesting employees install “necessary” integrations for compliance, security, or productivity purposes. Given the constant introduction of new tools in modern workplaces, employees rarely question such requests.
Why Insurance Companies Are Prime Targets
Scattered Spider’s focus on insurance companies is strategically sound from an attacker’s perspective:
High-Value Data Assets
Insurance companies possess some of the most valuable data for cybercriminals:
- Complete customer profiles including financial information
- Claims data revealing personal circumstances and vulnerabilities
- Underwriting information containing detailed risk assessments
- Business relationships and partnership details
Complex SaaS Ecosystems
Modern insurance operations rely heavily on interconnected SaaS applications:
- Customer relationship management systems
- Claims processing platforms
- Document management and collaboration tools
- Communication and video conferencing solutions
- Analytics and business intelligence platforms
Help Desk Vulnerabilities
Insurance companies often have large customer service operations with help desk systems—exactly the type of infrastructure Scattered Spider excels at compromising through social engineering.
Regulatory Compliance Pressure
The heavily regulated nature of the insurance industry creates urgency around compliance and security tools, making employees more likely to quickly approve integrations that claim to address regulatory requirements.
The European Expansion: A Predictable Pattern
Based on Scattered Spider’s historical attack patterns, we anticipate their insurance sector campaign will expand to European markets. Several factors support this prediction:
Historical Precedent
Scattered Spider has consistently followed a pattern of successful US attacks followed by international expansion:
- Casino attacks began in the US, then expanded globally
- Retail campaigns started in the UK, then spread to other markets
- The group’s English-speaking nature facilitates expansion to English-speaking markets and international businesses
GDPR Amplification
The European Union’s General Data Protection Regulation (GDPR) creates additional extortion opportunities. Data breaches involving EU citizens carry significant financial penalties, giving attackers additional leverage for ransom demands.
Similar SaaS Adoption Patterns
European BFSI organizations have adopted SaaS solutions at similar rates to their US counterparts, creating comparable attack surfaces and vulnerabilities.
Defense Strategies: Building Resilience Against SaaS-Based Attacks
Organizations must adapt their security strategies to address the realities of SaaS-based attacks:
OAuth Application Review Processes
Implement formal review processes for all third-party integrations:
- Require security team approval for new OAuth applications
- Maintain an inventory of all authorized integrations
- Regularly audit and remove unused applications
- Establish criteria for evaluating integration security
API Access Monitoring and Anomaly Detection
Deploy monitoring solutions that can identify suspicious API usage patterns:
- Unusual data access volumes or patterns
- Access to sensitive data by recently authorized applications
- API calls from unexpected geographic locations
- Bulk data extraction activities
Enhanced Employee Training
Security awareness training must evolve to address SaaS-specific threats:
- Recognition of sophisticated phishing campaigns
- Understanding of OAuth risks and proper authorization procedures
- Identification of social engineering tactics targeting SaaS integrations
- Proper escalation procedures for suspicious integration requests
Principle of Least Privilege for Integrations
Apply zero-trust principles to SaaS integrations:
- Grant minimum necessary permissions to third-party applications
- Implement time-limited access tokens where possible
- Regularly review and reduce application permissions
- Segregate sensitive data from general SaaS platforms
Help Desk Security Protocols
Strengthen help desk operations against social engineering:
- Implement multi-factor verification for sensitive requests
- Use out-of-band verification methods for identity confirmation
- Train staff to recognize and escalate suspicious requests
- Maintain detailed logs of all help desk interactions
DeepOpinion’s Commitment to Proactive Security
At DeepOpinion, we believe that understanding and preparing for emerging threats is essential for protecting both our organization and our customers. Our development of this proof-of-concept demonstrates our commitment to:
Continuous Threat Monitoring
Our security team actively monitors the evolving threat landscape, identifying emerging attack patterns and techniques that could impact our industry and customers.
Practical Security Research
We don’t just read about threats—we build practical demonstrations that help us understand attack methodologies and develop effective countermeasures.
Knowledge Sharing
By sharing our research and insights, we contribute to the broader security community’s understanding of emerging threats and defense strategies.
Customer Protection
Our proactive approach to threat research directly benefits our customers by ensuring our security measures evolve ahead of the threat landscape.
Looking Forward: The Evolution of SaaS Security
The Scattered Spider threat represents a fundamental shift in how we must think about enterprise security. Traditional perimeter-based security models are insufficient when the “perimeter” includes dozens or hundreds of SaaS applications, each with their own integration ecosystems.
Organizations must evolve their security strategies to address:
- The reality of distributed, cloud-native operations
- The complexity of modern identity and access management
- The human element in sophisticated social engineering attacks
- The need for continuous monitoring and adaptation
As Scattered Spider and similar threat actors continue to evolve their techniques, we will continue to research, analyze, and share our findings. The threat landscape is constantly changing, but through proactive research, practical demonstrations, and collaborative defense strategies, we can stay ahead of even the most sophisticated attackers.
The insurance industry’s current targeting by Scattered Spider serves as a wake-up call for all organizations operating in the modern SaaS ecosystem. By understanding these threats and implementing comprehensive defense strategies, we can protect our data, our customers, and our operations from even the most sophisticated attack methodologies.
The DeepOpinion Security Team continues to monitor the Scattered Spider threat and will provide updates as new intelligence becomes available. For questions about this research or to discuss security strategies for your organization, contact our security team via security@deepopinion.ai
Disclaimer: The proof-of-concept described in this post was developed for educational and security research purposes only. It was tested only in controlled environments with explicit authorization and should not be replicated without proper authorization and ethical considerations.


.png)
















